If you’re concerned about the development of Zero Trust Architecture, you’re not the only one. Cyberattacks evolve, and more organizations perform business online. It’s gradually becoming a requirement.
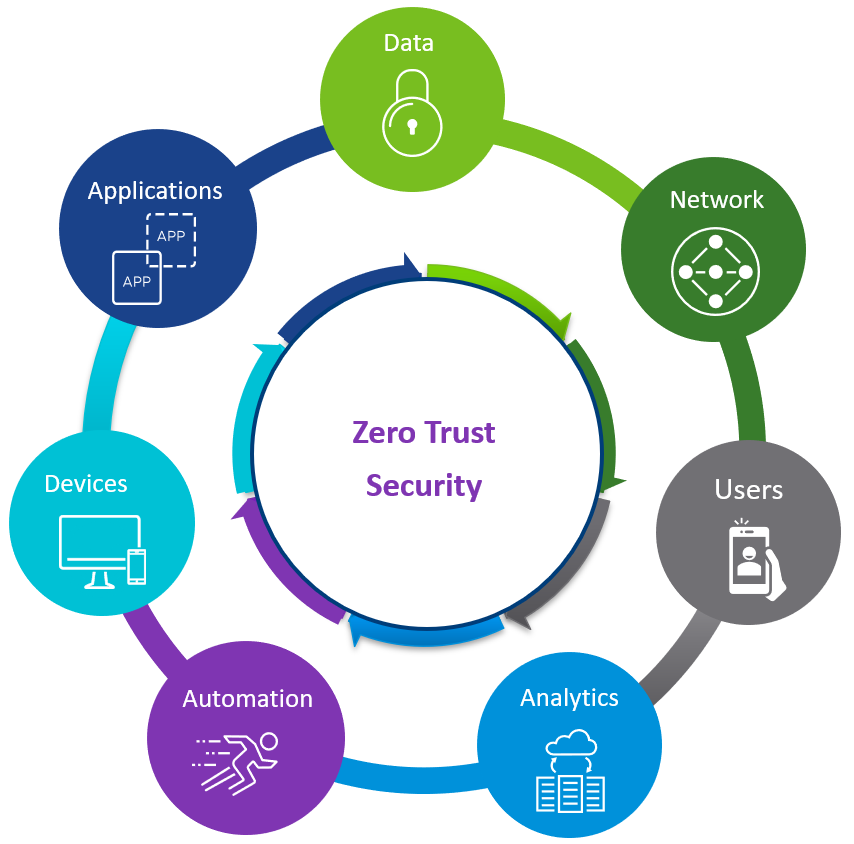
ZTA is a cybersecurity plan for an organization that incorporates zero trust concepts and includes component interactions, workflow planning, and access controls. As a result of a Zero Trust Architecture plan, a Zero Trust business has network infrastructure (both physical and virtual) and operational procedures in place. Zero Trust Architecture should be a business decision based on long-term goals like:
- Ease of administration
- Security controls that adapt to the situation
- Stakeholder accountability and cooperation
- Cybersecurity Risk Assessments and avoidance in general
Here are the fundamental principles that a successful Zero Trust Architecture deployment should follow within your organization.
- Ensure that all resources, regardless of location, are securely accessible.
- Use a Least Privilege Strategy and Enforce Access Control Strictly
- Examine and record all traffic

What are the practical steps in acquiring a ZTA:-
Adoption of the Zero Trust Architecture necessitates a new and dynamic access strategy. Other factors, such as a systemic organizational culture reform, will take more time and effort. The following are some practical considerations and preparation steps:
- Classification of Data
- Access Control Based on Roles
- Encrypted communications
- Cybersecurity Preparation
Architecture based on zero trust:-
Zero trust that acts as a framework for protecting modern companies has been around for years. Still, with the surge in cyberattacks, it’s gaining traction again. The following variables aid in determining which cybersecurity solutions provider are currently capable of providing a zero trust architecture.
1. Reliability:-
The ability of a zero-trust solution to measure from defending small and medium businesses to large-scale businesses is determined by how well its architecture is structured to adapt and flex to the changing needs of an organization. Protecting SMBs, which frequently function as independent partners to larger organizations, are, nevertheless, sometimes disregarded.
2. A track record of success:-
Cybersecurity solutions specialist must offer one or more means to get real-time insights and visibility across all endpoint assets, devices, and data repositories to excel at delivering a zero-trust solution and to ensure a track record of success.
3. Identity protection for humans and machines:-
Machine identities (including bots, robots, and IoT) grow twice as quickly as human identities. Machine-to-machine breaches have increased dramatically in the last 18 months, making securing machine identities using a least-privileged-access strategy a priority for any company.
4. Endpoint protection and IT asset tracking in real-time:-
Benchmarking zero trust merchants’ innovations — their capacity to go beyond the basics of endpoint security and create more resilient, persistent, and self-healing endpoints — is something that should be done.
Conclusion
Access points that require self-healing apps, security clients or agents, firmware, and operating systems require more automated methods. Enhanced visibility and control across IT and OT systems would benefit any organization. Leading zero-trust providers will provide references demonstrating their ability to deliver IT and OT insights.





